Xphere v2.0
Paul Kim
ABSTRACT
Traditional blockchain networks have faced challenges in overcoming the blockchain trilemma of scalability, security, and decentralization. To address this, we have designed a Dual-Chain Architecture consisting of the Main Chain and the Proof Chain.
The Main Chain ensures security and decentralization with a robust PoW consensus mechanism, while the Proof Chain focuses on scalability and efficient transaction processing. By dividing roles between the two chains, the architecture achieves a balance of trust and efficiency.
This innovative design supports diverse applications such as finance, logistics, and digital asset management, aiming to expand the potential of decentralized networks and drive the next generation of blockchain innovation.
Table of Contents
- Introduction
- Technical Specifications
- Dual-chain Architecture
- Consensus
- Economic Model of Coin
- Ethereum Compatibility in Xphere
- Conclusion
1. INTRODUCTION
The blockchain space has experienced rapid innovation, yet many networks face challenges in balancing accessibility, stability, and user adoption. Xphere 1.0 was introduced as a unique blockchain platform with its own smart contract structure, distinct from the commonly used EVM (Ethereum Virtual Machine) ecosystem. While this proprietary approach offered certain technical advantages, it also introduced significant limitations.
Key Limitations of Xphere 1.0:
- Limited Accessibility:
- The proprietary smart contract structure made it difficult for existing EVM developers and users to adopt the platform, hindering ecosystem growth.
- Transaction Drop Issues:
- Users often experienced dropped transactions, leading to frustration and reduced reliability for decentralized applications.
- Inconsistent Block Generation:
- Irregular block times created uncertainty for users and developers, impacting both usability and security.
These limitations not only restricted the growth of Xphere's ecosystem but also posed potential risks to its long-term adoption and scalability.
To address these challenges and unlock the full potential of the network, we developed Xphere v2.0, an upgraded blockchain platform designed to enhance accessibility, reliability, and scalability. By learning from the shortcomings of Xphere v1.0, Xphere v2.0 introduces a robust architecture that integrates dual-chain technology and significantly improves the user experience.
Xphere v2.0 is built with the following key objectives:
- Seamless integration with EVM-compatible tools and ecosystems, opening the network to a wider range of developers and users.
- Improved transaction reliability to eliminate dropped transactions and enhance overall network trust.
- Consistent block generation for predictable performance and better support for decentralized applications.
Xphere v2.0 represents a significant step forward, addressing the foundational challenges of its predecessor while paving the way for a more accessible and reliable blockchain ecosystem.
2. TECHNICAL SPECIFICATIONS
i. Network Architecture
Xphere's dual-chain architecture consists of the Main Chain and the Proof Chain. The Main Chain handles transaction processing and block finalization, while the Proof Chain focuses on validator selection and cryptographic proof generation.
ii. Node Requirements
To participate in the Xphere network, nodes must meet the following minimum requirements:
- CPU: 16 CPUs
- RAM: 32 GB
- Storage: 250 GB SSD
- Network: High-speed internet connection with at least 100 Mbps bandwidth
iii. Transaction Throughput
Xphere's architecture is designed to handle a high volume of transactions, with the Main Chain capable of processing up to 4,000 transactions per second (TPS).
3. DUAL-CHAIN ARCHITECTURE
i. Main Chain: Optimized PBFT Consensus
The Main Chain in Xphere's dual-chain architecture adopts an optimized version of the Practical Byzantine Fault Tolerance (PBFT) consensus mechanism. This design resolves critical challenges in scalability and communication overhead that traditional PBFT systems face, while maintaining robust security and decentralization.
Limitations of Traditional PBFT
PBFT is widely recognized for its fault tolerance and high security. However, as the number of participating nodes increases, its communication overhead grows exponentially. The consensus process requires multiple stages, including:
- Request: A client submits a transaction to the network.
- Pre-Prepare: The primary node broadcasts the transaction request to all other nodes.
- Prepare: Nodes verify the request and exchange their prepared status.
- Commit: Nodes exchange commit messages to finalize consensus.
- Reply: A consensus decision is sent back to the client.
In each stage, all nodes communicate with one another, resulting in excessive network traffic and resource consumption. This limitation has traditionally been mitigated by restricting the number of nodes participating in the consensus process, which risks reducing decentralization.
Xphere’s Solution: Council and Committee
To address these challenges, Xphere employs an optimized PBFT mechanism by introducing a Council and a Committee structure. This approach significantly reduces communication overhead while retaining the benefits of PBFT.
- Council Formation:
- The Council is a governing body comprising selected nodes in the network.
- Members are chosen based on predefined criteria to ensure decentralization and fairness.
- Dynamic Committee Selection:
- For each consensus round, a subset of Council members, the Committee, is randomly selected.
- The Committee handles the exchange of consensus messages, reducing the need for communication among all nodes.
- Efficient Consensus Communication:
- By confining message exchanges to the Committee, the communication load is drastically reduced.
- Even as the number of total nodes grows, the communication complexity remains constant or minimally affected.
Consensus Process in Xphere's Main Chain
The modified PBFT consensus mechanism in Xphere operates as follows:
- A client submits a transaction to the network.
- The Council receives the transaction and selects a Committee for the current round.
- The Committee exchanges and verifies consensus messages (e.g., Pre-Prepare, Prepare, Commit).
- Once consensus is reached, the Committee broadcasts the finalized decision to the network.
- The network responds to the client with the consensus result.
This streamlined process ensures efficient communication and predictable performance, even as the network scales.
Key Advantages
- Improved Scalability: By limiting consensus communication to the Committee, the network avoids the exponential growth in overhead seen in traditional PBFT systems.
- Enhanced Security: Randomized Committee selection adds unpredictability, reducing risks from targeted attacks.
- Decentralization Maintained: While the Committee conducts consensus, the Council ensures broad representation and fairness.
Comparison: Traditional PBFT vs. Xphere PBFT
| Feature | Traditional PBFT | Xphere PBFT |
|---|---|---|
| Communication Overhead | Exponential (O(n²)) | Limited to Committee (O(k²)) |
| Scalability | Poor as network size grows | Scalable with Council-Committee model |
| Decentralization | Reduced due to node limits | Retained with Council representation |
| Security | Strong but resource-intensive | Strong with randomized Committee |
Conclusion
By integrating the Council and Committee structure, Xphere’s Main Chain optimizes PBFT to meet the demands of modern blockchain ecosystems. This innovative approach not only ensures high performance and security but also lays the foundation for a scalable and decentralized future.
ii. Proof Chain: PoW-Based Validation Layer
The Proof Chain in Xphere's dual-chain architecture serves as a dedicated validation layer, designed to select validators and perform cryptographic proof computations. Utilizing the SHA-256 algorithm for its Proof-of-Work (PoW) operations, the Proof Chain ensures robust security and integrity within the network. Notably, transaction processing does not occur within the Proof Chain, as its sole purpose is to establish trust and validate validators efficiently.
Role of the Proof Chain
The Proof Chain's primary functions are:
- Validator Selection:
- The Proof Chain is responsible for determining which nodes are eligible to participate as validators within the network.
- This process is secured through cryptographic proof generated by PoW operations.
- Proof Generation:
- Using the SHA-256 algorithm, nodes solve complex computational puzzles to produce proofs.
- The produced proof is a verifiable output that establishes the validator’s eligibility.
- Supporting Security:
- The computational difficulty of PoW ensures that the network remains resistant to tampering and Sybil attacks.
- This layer acts as a foundation of trust for the network’s operation.
Understanding SHA-256
The SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function widely used in blockchain networks for its security and efficiency.
- How it Works:
- SHA-256 takes an input (e.g., a block of data) and processes it through a series of mathematical operations to generate a fixed-length, 256-bit hash.
- The hash is deterministic, meaning the same input will always produce the same output, but the output is seemingly random and unique.
- Why SHA-256 is Ideal for PoW:
- Collision Resistance: It is computationally infeasible to find two different inputs that produce the same hash.
- Pre-image Resistance: It is virtually impossible to derive the original input from the hash output.
- Efficient Verification: Once a hash is generated, it can be quickly and easily verified.
- Difficulty Adjustment: By requiring hashes to meet specific criteria (e.g., a certain number of leading zeros), the network can dynamically adjust the computational difficulty to control the time taken to find a valid proof.
Proof Chain Consensus Process
- Nodes compete to solve a PoW puzzle using the SHA-256 algorithm.
- The first node to generate a valid proof submits it to the network for verification.
- The proof is used to select the next validator(s) for the network.
- Once validators are selected, their role is passed to the Main Chain for transaction processing and block finalization.
Key Characteristics of the Proof Chain
- Dedicated Validation Layer:
- The Proof Chain does not handle transaction processing, ensuring its focus remains solely on validation and proof generation.
- Enhanced Security:
- By using SHA-256 and PoW, the Proof Chain provides robust protection against attacks, including Sybil attacks and tampering.
- Scalability through Specialization:
- Offloading the validation process to the Proof Chain allows the Main Chain to focus on transaction processing, improving overall network efficiency.
- Trust Foundation for the Main Chain:
- Validators selected through the Proof Chain provide a trusted basis for the Main Chain’s operations.
Advantages of the Proof Chain
| Feature | Benefit |
|---|---|
| Secure Validator Selection | Ensures only eligible nodes participate in consensus. |
| SHA-256 PoW Integration | Offers high security and verifiable proof generation. |
| Specialized Function | Avoids processing transactions, keeping the validation process lean. |
| Scalable Architecture | Allows the Main Chain to operate efficiently without validation overhead. |
Conclusion
The Proof Chain is an integral part of Xphere's dual-chain architecture, providing a secure and efficient mechanism for validator selection through SHA-256-based PoW operations. By isolating the validation process from transaction handling, the Proof Chain enhances network scalability and trustworthiness, laying a solid foundation for the Main Chain’s performance and reliability.
iii. Interaction Between Main Chain and Proof Chain
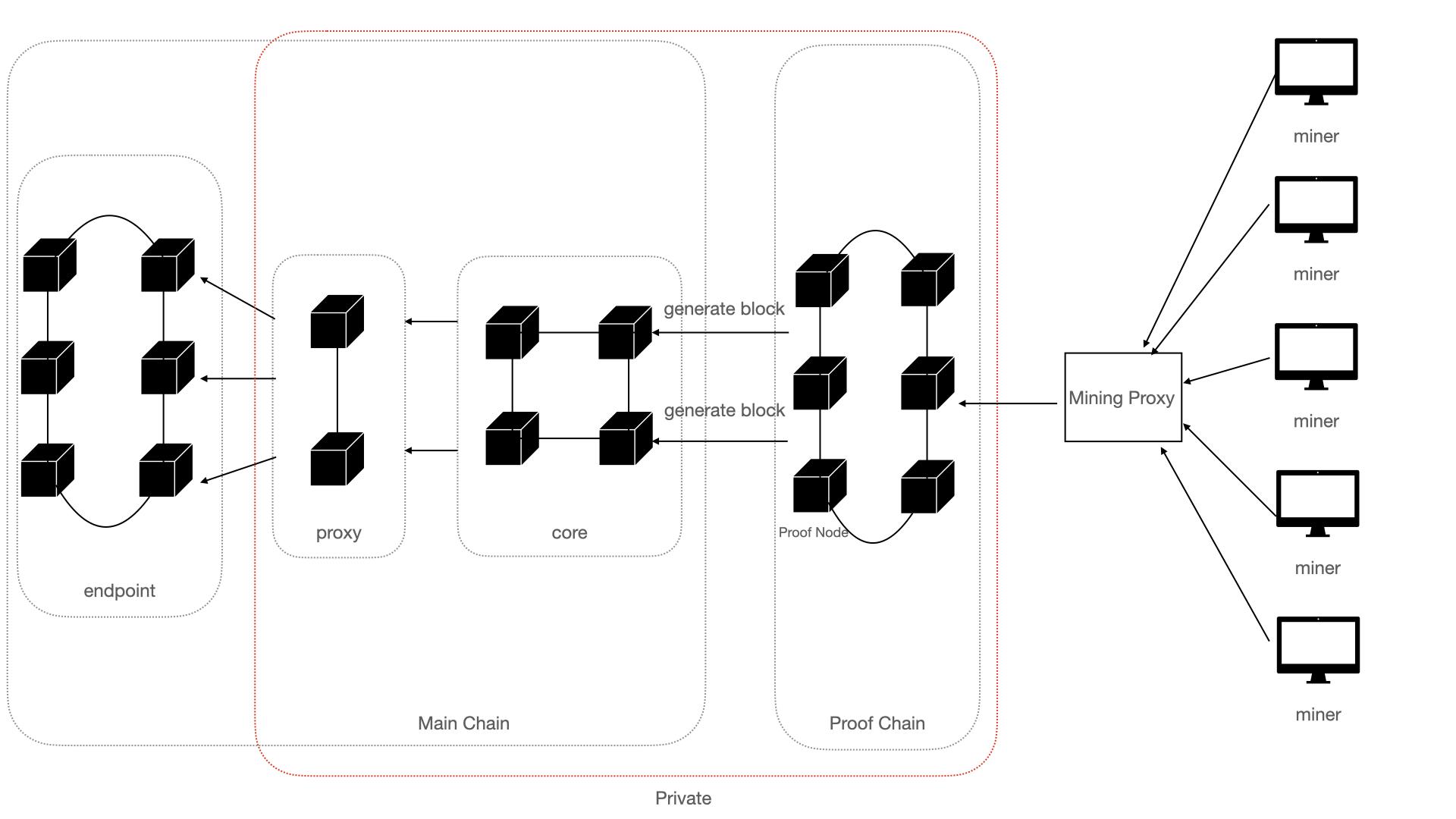
The Main Chain and Proof Chain in Xphere's dual-chain architecture operate in a tightly integrated manner, ensuring seamless communication and functionality. The two chains work collaboratively through algorithmic computations and RPC (Remote Procedure Call) communication to maintain a synchronized network state and facilitate validator selection.
Key Collaboration Mechanisms
- Status Synchronization via RPC Communication:
- The Proof Chain and Main Chain regularly exchange data through efficient RPC communication protocols.
- This process ensures that the current state of both chains remains synchronized, enabling real-time updates on validator statuses and system metrics.
- Validator Selection Coordination:
- The Proof Chain performs intensive SHA-256 PoW computations to generate proofs and determine eligible validators.
- These selected validators are then communicated to the Main Chain, which assigns them roles in block validation and consensus processes.
- The collaborative approach ensures fairness and reliability in validator selection, strengthening network security and decentralization.
- Algorithmic Data Exchange:
- Computation results, such as PoW proofs and validator scores, are dynamically shared between the chains.
- This exchange allows the Main Chain to make informed decisions about block production and consensus finalization.
Interaction Flow
- Proof Generation on the Proof Chain:
- Nodes compete to solve PoW challenges, and the Proof Chain generates cryptographic proofs.
- Validator Status Update via RPC:
- The Proof Chain shares validated proof data with the Main Chain.
- The Main Chain updates its validator registry based on the received data.
- Consensus Execution on the Main Chain:
- Validators selected by the Proof Chain participate in the Main Chain's consensus mechanism.
- This ensures a continuous and transparent validator rotation.
- State Feedback to the Proof Chain:
- The Main Chain provides feedback to the Proof Chain, including validator performance and system status, enabling adjustments in future validator selection processes.
Advantages of This Integration
| Feature | Benefit |
|---|---|
| Real-Time Synchronization | Maintains a consistent network state across both chains. |
| Secure Validator Selection | Ensures fairness and reliability through collaborative data exchange. |
| Efficient Resource Allocation | Offloads computation-heavy tasks to the Proof Chain, optimizing network performance. |
| Enhanced Scalability | Modular interaction between chains allows the network to scale seamlessly. |
Conclusion
The integration of the Main Chain and Proof Chain through algorithmic computations and RPC communication is a cornerstone of Xphere's dual-chain architecture. This collaboration enables secure, reliable validator selection and efficient state synchronization, ensuring the network operates cohesively and scales effectively to meet the demands of decentralized applications.
4. CONSENSUS
i. Consensus Mechanism: Trust and Security with Proof of Work (PoW)
Xphere's consensus mechanism is built on Proof of Work (PoW), a time-tested method that reinforces the network's trust and security. PoW leverages the computational power of participants to protect the blockchain from malicious activities while ensuring data integrity. In Xphere, this mechanism has been optimized to align with the network's dual-chain architecture, ensuring scalability and efficiency.
Core Principles of PoW
- Computational Effort:
- Validators compete to solve complex mathematical puzzles, a process requiring significant computational resources.
- The first validator to solve the puzzle gains the right to add a new block to the blockchain, driving the network's consensus.
- Verification of Work:
- The result of the computation (proof) can be easily verified by other nodes in the network, ensuring fairness and validity in the consensus process.
- Economic Incentives:
- Validators are rewarded for their computational efforts, creating a strong incentive for honest participation.
- The high cost of computation acts as a deterrent against malicious actions, as any attempt to manipulate the network would require disproportionate resources.
PoW and Network Security
- Resistance to Attacks:
- Sybil Attack Prevention: PoW requires computational resources that make it economically impractical for attackers to generate fake nodes at scale.
- 51% Attack Defense: Gaining control of the network’s majority computational power becomes infeasible as the network grows, ensuring security against hostile takeovers.
- Immutable Ledger:
- Altering the blockchain would require re-computing the PoW for all subsequent blocks, which becomes exponentially harder over time.
- Decentralized Trust:
- Trust is distributed across the network, removing the need for a centralized authority.
- The consensus process ensures that no single participant can manipulate the system.
Optimized PoW in Xphere
Xphere’s implementation of PoW is tailored to its dual-chain architecture, with enhancements to improve efficiency and scalability:
- Specialized Role in the Proof Chain:
- PoW is exclusively used in the Proof Chain for validator selection, allowing the network to offload computationally heavy tasks from the Main Chain.
- This separation ensures that the Main Chain remains optimized for transaction processing and block finalization.
- Efficient Computation Design:
- Xphere integrates SHA-256 as the cryptographic backbone of its PoW mechanism. This provides robust security through collision resistance and pre-image resistance while ensuring efficient validation of computational proofs.
- Energy Optimization:
- While maintaining PoW’s inherent security benefits, Xphere incorporates mechanisms to minimize computational waste, addressing common energy concerns associated with traditional PoW networks.
Benefits of PoW in Xphere
- Proven Security: PoW provides a secure and resilient consensus method, as demonstrated by leading blockchain networks like Bitcoin.
- Reliable Validation: Validators must perform verifiable computational work, minimizing fraudulent activities and maintaining the blockchain's integrity.
- Decentralization: PoW ensures the distribution of power across the network, reducing risks of centralization and enhancing trust among participants.
The Role of PoW in Xphere
In Xphere, PoW is a cornerstone of its validator selection process. The use of SHA-256 for computational tasks ensures a secure, fair, and transparent mechanism. By isolating validation tasks to the Proof Chain, Xphere enhances the Main Chain's efficiency, enabling the network to achieve high performance without compromising security or scalability.
ii. 51% Attack Mitigation in Xphere
Xphere's consensus mechanism is uniquely designed to eliminate the possibility of 51% attacks, a prevalent concern in PoW-based systems. By implementing controlled mining processes and randomized validator assignment, Xphere ensures an exceptionally secure and decentralized network.
Mechanisms to Prevent 51% Attacks
- Alliance-Restricted Mining:
- Only nodes approved by the Alliance are authorized to validate mining activities and participate in the PoW process.
- This restriction ensures that unauthorized or malicious nodes are completely excluded from the network.
- Randomized Miner-Validator Assignment:
- Miners cannot directly choose which Alliance node to submit their work to.
- The system dynamically assigns miners to Alliance nodes in a randomized manner, preventing collusion and manipulation.
- Separation of Miners and Alliances:
- Miners operate independently and have no influence over which Alliance node validates their work.
- This ensures that mining remains impartial and that no coordinated effort can target specific nodes.
Why This Design Matters
- Immunity to Coordinated Attacks:
To launch a 51% attack, an actor would need to control the majority of computational power in the network. Xphere’s Alliance-restricted mining and randomized assignments make this feat impossible. - Fair and Decentralized Validation:
The dynamic miner-validator assignment ensures that no entity can monopolize validation, reinforcing the network's decentralized nature. - Reliable Security Framework:
By combining controlled participation and unbiased validation, Xphere achieves a robust, trustless consensus system that safeguards the network from manipulation and attack.
This innovative approach secures Xphere against 51% attacks while maintaining decentralization and scalability, setting a new standard for blockchain security.
5. ECONOMIC MODEL OF THE COIN
As Xphere operates on its own mainnet, the native asset is classified as a coin rather than a token. The coin’s distribution, emission mechanism, and utility are carefully designed to ensure a sustainable and balanced ecosystem for the network's growth.
A. Coin Utility and Role in the Network
Xphere’s coin serves as the foundation of the ecosystem, enabling key functionalities such as:
- Transaction Fees:
- Used for processing and validating transactions on the Main Chain.
- Staking:
- Validators are required to stake coins to participate in consensus, ensuring alignment with the network’s security and integrity.
- Incentives for Miners and Alliances:
- Coins are rewarded to miners and Alliance nodes as part of the Proof Chain's operation, driving active network participation.
- Governance:
- Coin holders may participate in future governance mechanisms, influencing decisions related to network upgrades and policies.
B. Union Staking and Reward Mechanism
Xphere introduces a Union staking system that allows network participants to contribute to network security and governance while earning rewards through block validation activities.
Union Participation Requirements
- Staking Threshold:
- To participate as a Union member, participants must stake exactly 35 million XP coins.
- This substantial staking requirement ensures that only committed participants with significant network investment can join the Union.
- Node Address Registration:
- During the staking process, participants must provide a valid node address that will be associated with their Union membership.
- This node address serves as the identifier for reward distribution and network participation tracking.
Union Reward Distribution
- Block Proposer Selection and Rewards:
- When a Union member's node address is selected as a block proposer by the Proof Chain, that specific Union member receives 40% of the block reward for the proposed block.
- Reward Distribution Logic:
- The Proof Chain operates using a round-robin mechanism where validators are selected sequentially in a predetermined order.
- Union members participate in this round-robin cycle, and when their turn arrives, they serve as the block proposer for that specific block.
- Once a block is successfully validated, the Union member who serves as the proposer at the reward distribution moment on the Main Chain receives 40% of that block's reward automatically distributed to their registered node address.
- Round-Robin Validator Selection:
- The Proof Chain maintains a sequential order of all eligible Union validators in the round-robin cycle.
- Each Union member gets their turn to serve as block proposer based on this predetermined rotation.
- This systematic approach ensures fair distribution of proposer opportunities among all participating Union members.
- The round-robin mechanism guarantees that every Union member will have predictable chances to earn block rewards based on their position in the validation sequence.
Benefits of Union Participation
- Consistent Rewards: Regular block reward distribution provides stable income for committed network participants.
- Network Governance: Union members gain enhanced governance rights within the Xphere ecosystem.
- Long-term Value: The substantial staking requirement aligns Union members' interests with the network's long-term success.
- Security Contribution: Union staking enhances overall network security through increased stake-based participation.
C. Emission Mechanism
- Total Supply:
- The total coin supply is capped at 5.5 billion coins, combining the legacy token distribution with a long-term emission schedule.
- 1.5 billion coins were pre-distributed based on the total supply of Xphere 1.0, ensuring continuity for existing holders.
- The remaining 4 billion coins will be distributed over 100 years as mining and validation rewards.
- This structure ensures both scarcity and long-term value preservation.
- Deflationary Model:
- The emission follows a 26.28% annual reduction model, gradually decreasing the reward for miners and validators each year.
- This deflationary mechanism promotes scarcity, incentivizing early participation while maintaining economic stability over time.
- Block Reward System:
- Reward Adjustment Cycle: Block rewards are adjusted every 31,536,000 blocks, creating predictable emission cycles.
- Reward Distribution Frequency: Rewards are distributed every 60 blocks, ensuring regular and consistent compensation for network participants.
- Transaction-Based Rewards: Each block provides transaction-based rewards, creating direct incentives for transaction processing and network activity.
Emission Schedule Over 100 Years
The following table demonstrates the systematic reduction of mining rewards over a 100-year period:
| Year | Annual Mining Reward | Per Block Reward | Cumulative Supply |
|---|---|---|---|
| 0 | 0 | 0 | 1,500,000,000 |
| 1 | 1,051,200,000 | 2,000 | 2,551,200,000 |
| 2 | 774,944,640 | 1,474.4 | 3,326,144,640 |
| 3 | 571,289,188.608 | 1,086.92768 | 3,897,433,828 |
| ... | ... | ... | ... |
| 98 | 0.00015047 | 0.00000029 | 5,500,000,000 |
| 99 | 0.00011093 | 0.00000021 | 5,500,000,000 |
| 100 | 0.00008178 | 0.00000016 | 5,500,000,000 |
Total Reward Over 100 Years: 5,500,000,000 xp
Key Characteristics of the Emission Schedule:
- Predictable Decline: The 26.28% annual reduction creates a predictable and transparent emission curve
- Long-term Sustainability: The model ensures network incentives remain viable for decades while maintaining scarcity
- Early Adopter Advantage: Higher initial rewards incentivize early network participation and security
- Mathematical Precision: The emission schedule is algorithmically determined, ensuring fairness and transparency
D. Transaction Fee Burn Mechanism
Xphere implements a 50% transaction fee burn mechanism as a cornerstone of its sustainable economic model, designed to create long-term value preservation and network stability:
Balanced Deflation
- Controlled Network Activity Mitigation:
- The burn mechanism provides balanced deflationary pressure to prevent excessive network activity from causing inflationary effects.
- By permanently removing 50% of transaction fees from circulation, the system maintains economic equilibrium even during high-usage periods.
- Value Stability Through Appropriate Inflation Pressure Management:
- The burn mechanism works synergistically with the 26.28% annual emission reduction to ensure optimal inflation control.
- This dual-deflationary approach creates a stable foundation for long-term value preservation.
Validator Incentive Preservation
- Sufficient Validator Reward Maintenance:
- While 50% of fees are burned, the remaining 50% ensures validators receive adequate compensation for network security.
- This balance maintains strong validator participation essential for network integrity.
- Decentralized Consensus Mechanism Sustainability:
- The preserved portion of transaction fees supports the long-term viability of the consensus mechanism.
- Validators remain economically incentivized to maintain network security and performance.
Transparency and Predictability
- Clear and Reliable Burn Policy for Market Confidence:
- The fixed 50% burn rate provides market participants with transparent and predictable tokenomics.
- This clarity enhances investor confidence and supports informed decision-making within the ecosystem.
- Democratic Policy Decision Process Through Governance:
- Future adjustments to the burn mechanism can be implemented through community governance.
- This democratic approach ensures that policy changes reflect the collective interests of network participants.
Economic Impact and Benefits
The 50% burn mechanism creates several key advantages for the Xphere ecosystem:
- Usage-Based Scarcity: Higher network activity directly correlates with increased coin burns, creating a positive feedback loop between adoption and value preservation.
- Long-term Sustainability: The mechanism ensures that network growth contributes to coin scarcity rather than dilution, supporting sustainable economic growth.
- Market Stability: By providing predictable deflationary pressure, the burn mechanism helps stabilize coin value against market volatility.
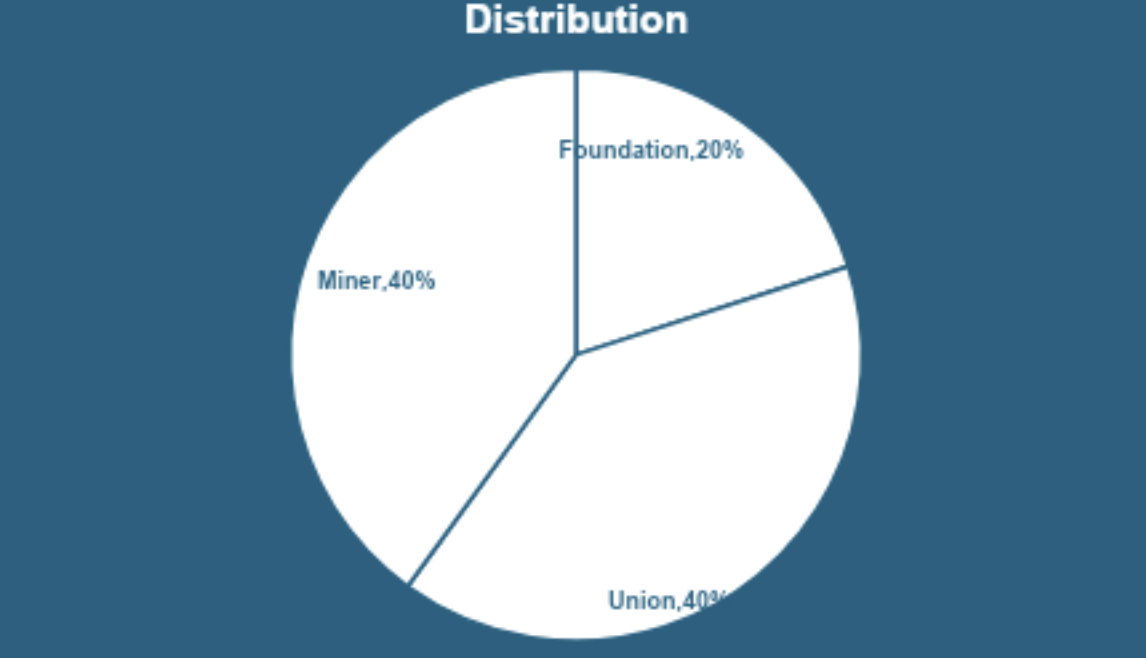
E. Distribution Model
Xphere coins are distributed in a manner that balances network operation, ecosystem growth, and community incentives:
6. ETHEREUM COMPATIBILITY IN XPHERE
Xphere is designed to ensure seamless compatibility with Ethereum, leveraging its established ecosystem while providing the scalability and flexibility of a next-generation blockchain. By supporting Ethereum's widely adopted EVM (Ethereum Virtual Machine) standard, Xphere opens its network to developers, tools, and decentralized applications (dApps) that already operate within the Ethereum ecosystem.
i. Key Aspects of Ethereum Compatibility
- EVM Compatibility:
- Xphere supports the execution of smart contracts written in Solidity, the primary programming language used on Ethereum.
- Developers can deploy existing Ethereum-based dApps directly on Xphere with minimal changes, reducing migration costs and time.
- Cross-Chain Interoperability:
- Xphere's architecture allows seamless interaction with Ethereum, enabling assets and data to move between the two networks.
- This interoperability creates a bridge for users and developers to leverage the strengths of both ecosystems.
- Tool Integration:
- Popular Ethereum tools such as MetaMask, Truffle, and Hardhat are fully compatible with Xphere, ensuring developers can use familiar workflows.
- This lowers the barrier to entry for developers transitioning to Xphere while maintaining a consistent user experience.
- Scalable Infrastructure:
- While maintaining compatibility with Ethereum, Xphere addresses Ethereum's scalability challenges by leveraging its dual-chain architecture.
- Xphere offers higher transaction throughput and lower fees, making it a viable alternative for dApps facing performance bottlenecks on Ethereum.
ii. Benefits of Ethereum Compatibility
- Access to a Large Ecosystem:
- By aligning with Ethereum standards, Xphere taps into the vast Ethereum developer community and its existing dApps, fostering rapid adoption.
- User and Developer Familiarity:
- Developers familiar with Ethereum can easily transition to Xphere without needing to learn a new language or framework.
- End-users benefit from a familiar wallet and dApp experience, ensuring a smooth onboarding process.
- Enhanced Performance for dApps:
- dApps running on Xphere enjoy faster transaction speeds and lower costs, addressing Ethereum's congestion and high gas fee issues.
iii. Building a Bridge Between Ecosystems
Xphere’s Ethereum compatibility ensures that it acts as a complementary network rather than a competing platform. By creating a bridge between the two ecosystems, Xphere enables developers and users to leverage Ethereum’s mature ecosystem alongside Xphere’s scalable and efficient infrastructure.
This strategic interoperability not only accelerates adoption but also positions Xphere as a critical player in the evolution of blockchain ecosystems, supporting both innovation and integration across networks.
7. CONCLUSION
Xphere represents a transformative step forward in blockchain technology, combining innovation, scalability, and robust security to address the limitations of existing networks. By introducing a dual-chain architecture that integrates the Main Chain and Proof Chain, Xphere achieves an optimized balance between scalability, security, and decentralization.
The Main Chain, with its PBFT-based consensus, ensures consistent block creation and high-speed transaction processing while maintaining decentralization through its Council and Committee structure. Simultaneously, the Proof Chain employs SHA-256-based PoW to deliver secure validator selection and trust through efficient computational proof mechanisms. Together, these chains form a cohesive and scalable foundation for the ecosystem.
Xphere also prioritizes interoperability and accessibility. By supporting Ethereum compatibility, Xphere bridges the gap between its innovative infrastructure and the vast Ethereum ecosystem. Developers and users can seamlessly leverage familiar tools, dApps, and workflows while benefiting from Xphere's superior performance and efficiency.
The coinomics of Xphere further underscores its sustainability, with a capped supply of 5.5 billion coins, a deflationary model reducing emission by 26.28% annually, and a strategic distribution model that balances incentives for miners, Alliances, and the Foundation. This economic model not only encourages early participation but also ensures long-term network health and value retention.
Xphere's comprehensive approach to network security includes unique mechanisms to prevent 51% attacks by restricting mining to Alliance-approved nodes and randomizing miner-to-validator assignments. These measures guarantee the network’s resilience against malicious activities while promoting a trustless and decentralized ecosystem.
In conclusion, Xphere is not just a blockchain platform but a foundational infrastructure for the next generation of decentralized applications and services. Its innovative architecture, robust security, seamless Ethereum compatibility, and sustainable economic model make Xphere a pivotal player in shaping the future of blockchain technology. With a clear vision and a strong technical foundation, Xphere is poised to drive adoption and innovation, fostering a new era of decentralized ecosystems.